NIST public draft Cybersecurity Framework 2.0 initial analysis
by Gilad Bandel | August 10, 2023
Introduction
The National Institute of Standards and Technology (NIST) has recently released the public draft of Cybersecurity Framework (CSF) 2.0, open for comments until November 4, 2023. This version follows the previously published CSF 1.1 from 2018.
Major Changes in CSF 2.0
CSF 2.0 introduces two significant updates that warrant attention. Firstly, the inclusion of the GOVERN function alongside associated categories and subcategories. Secondly, the refinement, reorganization, classification adjustments, and other enhancements have been made to streamline the framework.
In this analysis, our focus will be on the newly introduced GOVERN function, as it stands out as the pivotal change within the framework.
Retrospective at CSF 1.1
Considering the historical context, CSF version 1.1 provided a comprehensive breakdown of the following functions:
-
IDENTIFY (ID) - Develop an organizational understanding to manage cybersecurity risk to systems, people, assets, data, and capabilities
-
PROTECT (PR) - Develop and implement appropriate safeguards to ensure delivery of critical services
-
DETECT (DE) - Develop and implement appropriate activities to identify the occurrence of a cybersecurity event
-
RESPOND (RS) - Develop and implement appropriate activities to take action regarding a detected cybersecurity incident
-
RECOVER (RC) - Develop and implement appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident
The subsequent chart illustrates these functions and their iterative, continuous workflow.
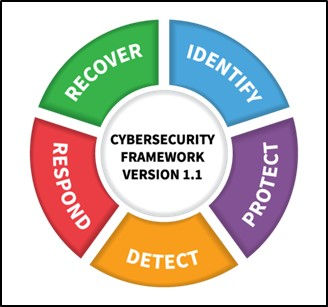
Cybersecurity Framework Version 1.1
Initially, the assumption was that this process could be implemented and autonomously managed as vaguely described in section 2.4 of SCF 1.1 - Coordination of Framework Implementation. While the concepts and functions outlined in CSF 1.1 hold immense value, adopting these best practices undoubtedly enhances the security of the system. However, it has become evident that relying on a “spontaneous” and self-organizing approach is insufficient. Hence, the necessity for a central coordinating function arises to effectively oversee the entire process.
Focus on the New GOVERN Function
This analysis primarily delves into the novel GOVERN function due to its pivotal role in the updated CSF 2.0. The evolution from CSF 1.1's functions – IDENTIFY, PROTECT, DETECT, RESPOND, and RECOVER – has led to the emergence of GOVERN as a central coordinating entity. It orchestrates the entire cybersecurity process by providing oversight and direction.
Structural Modifications in CSF 2.0
The revised framework below illustrates the new GOVERN function as a distinctive concentric yellow hollow disk.
Cybersecurity Framework Version 2.0
The functions and definitions in CSF 2.0 are as follows:
-
GOVERN (GV) - Establish and monitor the organization’s cybersecurity risk management strategy, expectations, and policy
-
IDENTIFY (ID) - Help determine the current cybersecurity risk to the organization
-
PROTECT (PR) - Use safeguards to prevent or reduce cybersecurity risk
-
DETECT (DE) - Find and analyze possible cybersecurity attacks and compromises
-
RESPOND (RS) - Take action regarding a detected cybersecurity incident
-
RECOVER (RC) - Restore assets and operations that were impacted by a cybersecurity incident
Scope of the GOVERN Function
The GOVERN function is strategically designed to encompass various aspects of organizational context and risk management. This includes:
-
Risk management strategy
-
Cybersecurity supply chain risk management
-
Roles, responsibilities, and authorities
-
Policies, processes, and procedures
-
Oversight
Categorized Elements within GOVERN
The categories under the GOVERN function are structured as follows:
-
Organizational Context (GV.OC): The circumstances — mission, stakeholder expectations, and legal, regulatory, and contractual requirements — surrounding the organization’s cybersecurity risk management decisions are understood (formerly CSF 1.1 ID.BE)
-
Risk Management Strategy (GV.RM): The organization’s priorities, constraints, risk tolerance and appetite statements, and assumptions are established, communicated, and used to support operational risk decisions (formerly CSF 1.1 ID.RM)
-
Cybersecurity Supply Chain Risk Management (GV.SC): Cyber supply chain risk management processes are identified, established, managed, monitored, and improved by organizational stakeholders (formerly CSF 1.1 ID.SC)
-
Roles, Responsibilities, and Authorities (GV.RR): Cybersecurity roles, responsibilities, and authorities to foster accountability, performance assessment, and continuous improvement are established and communicated (formerly CSF 1.1 ID.GV-02)
-
Policies, Processes, and Procedures (GV.PO): Organizational cybersecurity policies, processes, and procedures are established, communicated, and enforced (formerly CSF 1.1 ID.GV-01)
-
Oversight (GV.OV): Results of organization-wide cybersecurity risk management activities and performance are used to inform, improve, and adjust the risk management strategy
Interplay with CSF 1.1 Functions
It is essential to emphasize that the creation of the GOVERN function does not negate the preexistence and relevance of functions from CSF 1.1. This highlights GOVERN's role as a linchpin that interconnects all functions. In numerous instances, complete categories and subcategories have been transferred from other functions, with a notable emphasis on the IDENTIFY function as the source. An illustrative example can be found in the document's Appendix C, Table 5, where the GOVERN subcategory is highlighted:
-
GV.OC-01: The organizational mission is understood and informs cybersecurity risk management is based on formerly CSF 1.1 IDENTIFY subcategories ID.BE-02 and ID.BE-03
-
GV.RM-02: Risk appetite and risk tolerance statements are determined, communicated, and maintained is based on formerly CSF 1.1 IDENTIFY subcategories ID.RM-02, ID.RM-03
-
Etc.
-
Broadly speaking, a significant number of subcategories within the new GOVERN function were inherited from CSF 1.1's IDENTIFY function, although exceptions exist. However, the crux of the matter is not solely in enumerating these interrelated subcategories. Instead, it lies in the acknowledgment of GOVERN as a distinct and crucial entity, deserving of its independent recognition. Notably, GOVERN holds an intrinsic connection to all pre-existing functions within the framework.
Definition of GOVERN
GOVERN (GV) – Establish and monitor the organization’s cybersecurity risk management strategy, expectations, and policy. The GOVERN Function is cross-cutting and provides outcomes to inform how an organization will achieve and prioritize the outcomes of the other five Functions in the context of its mission and stakeholder expectations. Governance activities are critical for incorporating cybersecurity into an organization’s broader enterprise risk management strategy. GOVERN directs an understanding of organizational context; the establishment of cybersecurity strategy and cybersecurity supply chain risk management; roles, responsibilities, and authorities; policies, processes, and procedures; and the oversight of cybersecurity strategy.
Relationship with Other Functions
The GOVERN function collaborates closely with other functions, particularly IDENTIFY. Understanding organizational context and associated risks facilitates a targeted approach aligned with the organization's risk management strategy.
… and the related cybersecurity risks enables an organization to focus and prioritize its efforts in a manner consistent with its risk management strategy and the mission needs identified under GOVERN.
Moreover, the remaining functions also maintain a symbiotic relationship with GOVERN, exemplified by:
Investments in planning and testing in the GOVERN and IDENTIFY Functions will support timely incident response and recovery actions for cybersecurity incidents in the RESPOND and RECOVER Functions. GOVERN is in the center of the wheel because it informs how an organization will implement the other five Functions.
Implementation and Importance
Implementing GOVERN is not a one-size-fits-all process; each organization should tailor its approach based on available information, profile and risk appetite. Top management's involvement in this step significantly influences the framework's subsequent implementation and execution, both internally and across the supply chain.
Automation and Synergies
To facilitate this process, automation tools like Enterprise Risk Management (ERM) play a crucial role. Furthermore, harmonizing with other relevant standards, such as ISO/SAE 21434:2021 Cybersecurity Engineering, specifically the Threat Analysis and Risk Assessment (TARA) part, enhances the effectiveness of the process.
Conclusions and key takeaways
-
NIST CSF 2.0 represents a significant leap forward in the landscape of automotive cybersecurity. We strongly encourage you to engage in a comprehensive review of the document and contribute your valuable insights. Once ratified, adopt it in your organization.
-
At the heart of this transformation is the introduction of the GOVERN function, a pivotal change that orchestrates, coordinates, correlates, and oversees the entire cybersecurity process.
-
To ensure both a cybersecure vehicle and adherence to regulations such as UNR 155, the implementation of industry guidelines, best practices (including NIST CSF, Auto-ISAC, NHTSA, ENISA, etc.), and standards (such as ISO/SAE 21434:2021) is of paramount importance.
-
Recognizing the intricate nature of automotive cybersecurity, the integration of automation tools is essential for achieving efficiency, effectiveness, top-notch quality, and cost-effectiveness in the process.
To delve further into enhancing your automotive cybersecurity stance, streamlining processes through automation, optimization, and refining practices like cybersecurity TARA, we invite you to explore our toolset. Witness a live demonstration of these solutions by reaching out to us at info@systemweaver.com.
About the Author
Gilad Bandel is the VP of Cybersecurity at SystemWeaver (https://www.systemweaver.com/), leading efforts in delivering innovative automotive cybersecurity solutions. With over three decades of experience in the automotive, cybersecurity, and networking sectors, Gilad is a respected figure known for his expertise in go-to-market strategies, especially in the fields of cybersecurity solutions for automotive, IoT, critical infrastructure, and homeland security.
Reference: National Institute of Standards and Technology (2023) The NIST Cybersecurity Framework 2.0. (National Institute of Standards and Technology, Gaithersburg, MD), NIST Cybersecurity White Paper (CSWP) NIST CSWP 29 ipd. https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.29.ipd.pdf